INFORMATION SYSTEMS. COMPUTER SCIENCES. ISSUES OF INFORMATION SECURITY
- The comparison of machine learning methods reveals the varying effectiveness of anomaly detection methods used to detect cyber threats and deviations in electrical systems.
- Isolation Forest is best at detectingabrupt changes related to cyberattacks with high accuracy and a minimum of false positives.
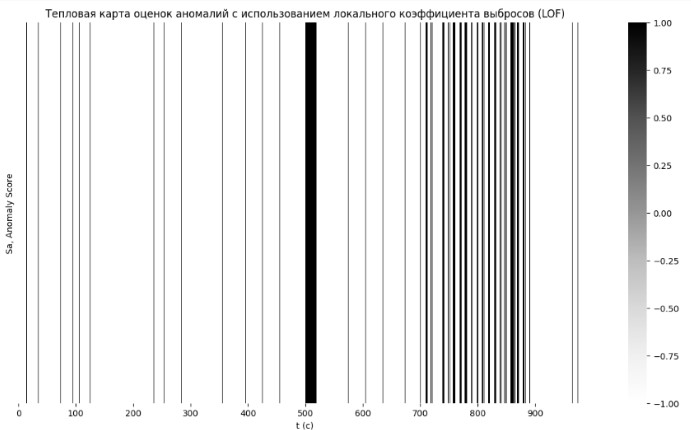
- LOF can also be effective in detecting cyberattacks, its increased sensitivity to minor deviations increases the number of false positives.
- K-means and One-Class SVMs are less effective in detecting abrupt anomalies but are useful for general clustering of data and detecting both abrupt and smooth changes, respectively.
- The obtained research results indicate the advantages of using a combination of machine learning algorithms to ensure the reliable protection of smart networks from cyberattacks taking into account the nature of the electrical load.
Objectives. The transformation of modern electric grids into decentralized smart grids presents new challenges in the field of cybersecurity. The purpose of this work is to conduct research and analysis into the effectiveness of different machine-learning methods for identifying anomalies in decentralized smart networks, including cyberattacks and emergency modes, as well as to develop recommendations on the optimal combination of these methods for ensuring effective cybersecurity under conditions of changing electrical loads.
Methods. We consider several machine learning methods for identifying anomalies in power systems that simulate network behavior under conditions of cyberattacks and emergency modes. The relative effectiveness of such methods as multifractal analysis using wavelets, the Isolation Forest model, local outlier factor (LOF), k-means clustering, and one-class support vector machine (One-Class SVM), is analyzed.
Results. The comparison of machine learning methods reveals the varying effectiveness of anomaly detection methods used to detect cyber threats and deviations in electrical systems. Isolation Forest is best at detecting abrupt changes related to cyberattacks with high accuracy and a minimum of false positives. While LOF can also be effective in detecting cyberattacks, its increased sensitivity to minor deviations increases the number of false positives. K-means and One-Class SVMs are less effective in detecting abrupt anomalies but are useful for general clustering of data and detecting both abrupt and smooth changes, respectively.
Conclusions. The obtained research results indicate the advantages of using a combination of machine learning algorithms to ensure the reliable protection of smart networks from cyberattacks taking into account the nature of the electrical load.
- The study considers the structure of modern multicore microprocessors as the basis for building computing modules of cluster computing systems (CSs). As the number of cores in the microprocessor structure increases, the communication network which unites them into a single structure becomes more complicated.
- It has been shown that in new developments of microprocessors, communication between cores is performed in the form of a network. The microprocessors themselves are MIMD structures in accordance with the well-known Flynn classification.
- The proposed method of selecting an effective structure of a CS allows us to obtain the optimal structure of a CS according to the criterion of performance.
Objectives. Analysis of the various architectures of computing systems (CSs) used in recent decades has allowed us to identify the most common structures. One of the key features is the use of mass-produced equipment to create data processing subsystems (for example, multicore processors and high-capacity semiconductor memory), as well as network equipment to build communication subsystems. This reduces hardware costs and allows typical or cluster configurations to be created, which is especially important for expensive CSs. The desire to achieve high computational speed and performance in such CSs requires minimizing the time to complete the task and balancing time delays both in data processing subsystems and in the communication subsystem which provides data transmission inside the CS. The aim of this work is to analyze computing modules (CMs) and structures on the basis of which the construction of cluster CSs is carried out.
Methods. The main results of the work were obtained using methods of mathematical analysis and modeling.
Results. The study considers the structure of modern multicore microprocessors as the basis for building CMs of cluster CSs. As the number of cores in the microprocessor structure increases, the communication network which unites them into a single structure becomes more complicated. It has been shown that in new developments of microprocessors, communication between cores is performed in the form of a network. The microprocessors themselves are MIMD structures in accordance with the well-known Flynn classification.
Conclusions. The proposed method of selecting an effective structure of a CS allows us to obtain the optimal structure of a CS according to the criterion of performance.
- A numerical study of packet transfer processes between central processing stations in the FDDI network is conducted. The processes of discrete information exchange between electronic devices in the system of electrical digital substations are considered.
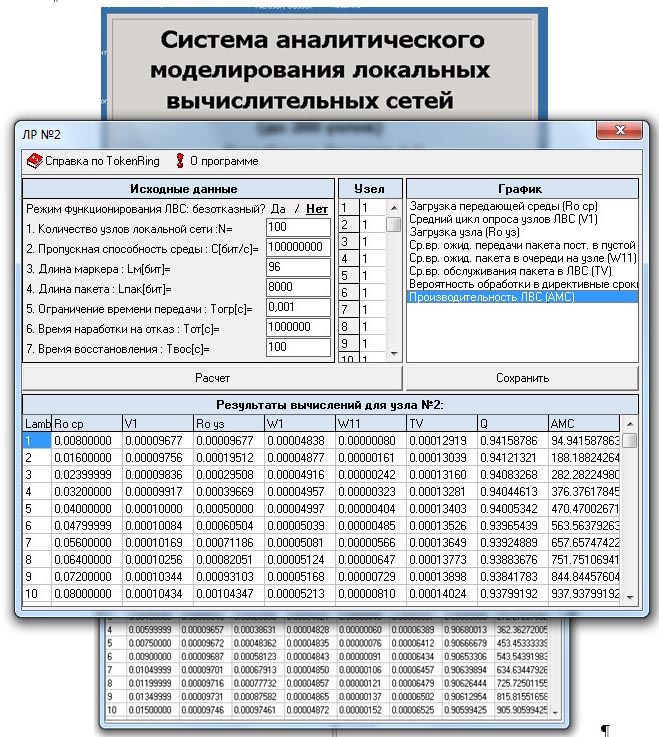
- The authors calculated node loading dependencies, FDDI network performance and temporal characteristics of the packet transfer processes on the incoming message flow intensity and the transmission medium reliability.
- The existence of the critical operating network region was established, which leads to a sharp increase in node load and temporal characteristics, while performance reaches its maximum value and then sharply decreases.
Objectives. To develop analytical approaches for the evaluation of probability-time characteristics and fiber distributed data interface (FDDI) network performance with the marker access method, thus enabling communication processes for digital electrical substations to be automated.
Methods. The authors used theory reliability methods, random process theory, mass maintenance theory, the Laplace–Stieltjes transformation for inferring functional equations and the probability-time characteristics calculation for the information transfer processes with the occurring failures.
Results. We conducted a numerical study of packet transfer processes between central processing stations in the FDDI network. We considered the processes of discrete information exchange between electronic devices in the system of electrical digital substations. These included the main technological operations and electrical digital substations operator performed when preparing reports. We described the different modes of operation, both for the individual electrical digital substation and for the system. The authors calculated node loading dependencies, FDDI network performance and temporal characteristics of the packet transfer processes on the incoming message flow intensity and the transmission medium reliability. We conducted a functional analysis of the FDDI networks on two fiber-optic rings which form the main and redundant path of data transfer between the network nodes, significantly increasing network resiliency. The objective of the study was to analyze the information transfer processes in FDDI networks with an accent on ensuring the transmission medium reliability.
Conclusions. We were able to establish the existence of the critical operating network region, which leads to a sharp increase in node load and temporal characteristics, while performance reaches its maximum value and then sharply decreases. We propose the exchange of discrete messages to reflect the electronic devices state and information messages of operator between various remotely spaced electrical digital substation with the FDDI fiber-optic network.
- The model for managing information security incidents within an enterprise which optimizes incident management by minimizing damage and costs is proposed.
- The incident criticality, available resources, response time, and the likelihood of successful incident resolution are considered.
- Testing of the model on synthetic data showed that the proposed approach significantly improves the selection of optimal actions for responding to incidents in situations constrained by budget and time limitations, thereby enhancing the overall effectiveness of incident management.
Objectives. The primary aim of the study is to develop a model for managing information security incidents within an enterprise that minimizes damage and costs associated with incident resolution under limited resources and time constraints.
Methods. The paper analyzes existing approaches to managing information security incidents, including mathematical and simulation models, stochastic differential equations, Markov chains, and other methods. The study is based on a systems approach, incorporating analysis of incident parameters, actions for their resolution, response times, damages due to incident occurrence, and the probability of incident elimination. To validate the developed model, synthetic data reflecting various types of incidents and possible actions were used.
Results. The proposed model optimizes incident management by minimizing damage and costs. It considers parameters such as incident criticality, available resources, response time, and the likelihood of successful incident resolution. Testing of the model on synthetic data showed that the proposed approach significantly improves the selection of optimal actions for responding to incidents in situations constrained by budget and time limitations, thereby enhancing the overall effectiveness of incident management.
Conclusions. Implementing the proposed model in enterprises will improve the overall level of information security, enhance incident response efficiency, and strengthen information protection processes. This will ensure the minimization of risks associated with data leaks and other incidents, thus helping enterprises to make informed and timely decisions under conditions of limited resources and time.
MODERN RADIO ENGINEERING AND TELECOMMUNICATION SYSTEMS
- The aim of the work is to develop a type of recursively separable digital filter with variable sizes of a scanning multi-element aperture which allows the number of computational operations to be reduced while maintaining the efficiency of filtering input data (images).
- An algorithm for the recursive-separable implementation of a digital filter is described, and the final view of the processing aperture and its three-dimensional appearance are presented.
- In order to evaluate the performance of the filter, a comparison of the developed algorithm with the classical two-dimensional convolution algorithm was carried out.
- The study established that the processing time of a test image using the developed filter is on average 5 times less than the time taken by the classical two-dimensional convolution algorithm.
Objectives. The main aim of digital image processing is to increase clarity while maintaining image quality and eliminate noise. However, the amount of information contained in digital image files is growing year after year. This circumstance negatively affects processing time, critical for systems with high load requirements on the computing platform. In this regard, the use of digital filters which enable a reduction to the processing time of incoming data is important. In order to resolve this issue, adaptive filters with different sizes of multielement processing aperture are being developed to improve image clarity and preserve image details. Filters with adaptive properties are able to change their parameters during data processing, and provide maximum performance as the aperture size increases. The aim of the work is to develop a type of recursively separable digital filter with variable sizes of a scanning multielement aperture which allows the number of computational operations to be reduced while maintaining the efficiency of filtering input data (images).
Methods. The work used recursive-separable methods and algorithms to construct digital filters.
Results. An algorithm for the recursive-separable implementation of a digital filter is described, and the final view of the processing aperture and its three-dimensional appearance are presented. In order to evaluate the performance of the filter, a comparison of the developed algorithm with the classical two-dimensional convolution algorithm was carried out. The experiment was performed using images of various sizes and consisted of determining the time spent on the process of processing the test image. The study established that the processing time of a test image using the developed filter is on average 5 times less than the time taken by the classical two-dimensional convolution algorithm. The optimal coefficients for magnifying the central element and raising the positive part of the aperture of a digital filter were determined, enabling the efficiency of its use to be enabled.
Conclusions. The studies show the effectiveness of using the developed recursive-separable two-dimensional filter to improve image clarity and reduce the time spent on processing.
MICRO- AND NANOELECTRONICS. CONDENSED MATTER PHYSICS
- When measuring the transverse Kerr effect on thin-film structures, interference effects have a great influence on the result obtained.
- The simulation results show that interference effects in different parts of the spectrum when using white light sources do not neutralize each other. The magnitude of the effect is affected not only by the thickness of the structure layers, but also by the shape of the source emission spectrum, as well as the sensitivity curve of the photodetector.
- The output of the measured value of the effect to a plateau at relatively large thicknesses of the magnetooptical film is due to the light being absorbed in the thickness of the magneto-optical film and is negligibility of the back reflection of light from the substrate.
Objectives. When measuring the transverse Kerr effect on thin-film structures, interference effects have a great influence on the result obtained. In conference presentations, some researchers have reported on the use of white light in experiments. In their opinion, despite the thickness of the studied layers being much less than the wavelength of light, white light can help avoid interference effects and/or resonant excitation of plasmon waves. The aim of the present work is to verify the validity of such statements using simulation.
Methods. In order to solve this problem, the method of computer simulation was used. A numerical solution of equations was compiled for a model structure for various thicknesses and materials of layers.
Results. The simulation results show that interference effects in different parts of the spectrum when using white light sources do not neutralize each other. The magnitude of the effect is affected not only by the thickness of the structure layers, but also by the shape of the source emission spectrum, as well as the sensitivity curve of the photodetector. In this case, the output of the measured value of the effect to a plateau at relatively large thicknesses of the magnetooptical film is due to the light being absorbed in the thickness of the magneto-optical film and is negligibility of the back reflection of light from the substrate.
Conclusions. The presented technique takes into account the influence of interference effects when measuring the equatorial Kerr effect in white light or using other sources having a wide spectral range, thus improving the interpretation of experimental results. The results are relevant to the development and research of the physical foundations for creating new and improving existing devices in micro-, nano-, and solid-state electronics, as well as quantum devices, including optoelectronic devices and converters of physical quantities.
- The angular reflection spectrum of linearly polarized electromagnetic waves from a multilayer periodic mirror on a transparent substrate is studied.
- The exact analytical expressions for reflection and transmission coefficients generalizing the cases of incidence of plane transverse electric and transverse magnetic modes on limited periodically structured media with a stepped refractive index profile are derived.
- Reflection of linearly polarized radiation is considered for a flat boundary of two dielectrics, a thin plane-parallel plate, and a multilayer dielectric mirror.
- The obtained expressions for the transmission coefficient of a confined one-dimensional photonic crystal, which are shown to be determined by the interference of Floquet–Bloch waves presented in the form of inhomogeneous waves, can be reduced to a form analogous to the expression for the value of the transmission coefficient of a traditional Fabry–Pérot interferometer.
Objectives. The purpose of the article is to carry out a theoretical and experimental study of the angular reflection spectrum of linearly polarized electromagnetic waves from a multilayer periodic mirror on a transparent substrate to exact analytical expressions for reflection and transmission coefficients generalizing the cases of incidence of plane transverse electric (TE) and transverse magnetic (TM) modes on limited periodically structured media with a stepped refractive index profile.
Methods. The theoretical analysis of the reflection problem is based on the search for exact analytical solutions in the form of Floquet–Bloch waves presented in the form of inhomogeneous waves in the domain of periodically structured media. On the basis of the possible existence of a single Floquet–Bloch wave in a limited onedimensional photonic crystal, it is proposed to search for exact solutions of the wave equation in the form of a linear combination of inhomogeneous waves propagating in different directions. By using the canonical forms of the considered periodic structures, it is possible to carry out the simple transition from the case of TE polarization to TM type in dispersion relations and expressions for the angular reflection spectrum.
Results. Cases of reflection of linearly polarized radiation are considered for the following cases: a flat boundary of two dielectrics, a thin plane-parallel plate, and a multilayer dielectric mirror. Exact analytical expressions for the reflection and transmission coefficients generalizing the cases of incidence of TE and TM polarizations waves on a limited one-dimensional photonic crystal are obtained. The transmission coefficients of a plane TE wave from a multilayer dielectric mirror sputtered on thin glass were experimentally measured.
Conclusions. A quantitative and qualitative agreement of experimental measurements of the transmission coefficient of a plane wave incident from a half-space on a confined photonic crystal with theoretical calculations is obtained. The obtained expressions for the transmission coefficient of a confined one-dimensional photonic crystal, which are shown to be determined by the interference of Floquet–Bloch waves presented in the form of inhomogeneous waves, can be reduced to a form analogous to the expression for the value of the transmission coefficient of a traditional Fabry–Pérot interferometer. In the case of TM polarization, when the Brewster condition is fulfilled at the interlayer boundaries, the Floquet–Bloch wave has the form of homogeneous plane waves in the layers of a photonic crystal.
MATHEMATICAL MODELING
- New integro-differential relations are proposed based on linear rheological models for the Maxwell medium and the Kelvin medium, including both dynamic and quasi-static models for viscoelastic and elastic media, generalizing the results of previous studies.
- The proposed constitutive relations of the new form are applicable to describe the thermal response of quasi-elastic bodies of a canonical shape simultaneously in three coordinate systems with a system-defining parameter, which makes it possible to identify the influence of the topology of the region on the value of the corresponding temperature stresses.
Objectives. In recent decades, the relevance of research into the thermal response of solids to a temperature field has increased in connection with the creation of powerful energy emitters and their use in technological operations. There is a significant number of publications describing these processes using mathematical models of dynamic or quasi-static thermoelasticity, mainly for most technically important materials that obey Hooke’s law. However, at elevated temperatures and higher stress levels, the concept of an elastic body becomes insufficient: almost all materials exhibit more or less clearly the phenomenon of viscous flow. The real body begins to exhibit elastic and viscous properties and becomes viscoelastic. A rather complex problem arises: the development of dynamic (quasistatic) thermoviscoelasticity within the framework of the corresponding mathematical models of classical applied thermomechanics and mathematics. The purpose of the work is to consider the open problem of the theory of thermal shock in terms of a generalized model of thermoviscoelasticity under the conditions of classical Fourier phenomenology on the propagation of heat in solids. Three types of intense heating are considered: temperature, thermal, and medium heating. Intensive cooling modes can be equally considered. The task is posed: to develop model representations of dynamic (quasi-static) thermoviscoelasticity that allow accurate analytical solutions of the corresponding boundary value problems on their basis. This direction is practically absent in the scientific literature.
Methods. Methods and theorems of operational calculus were used.
Results. Model representations of the thermal response of viscoelastic bodies using the proposed new compatibility equation in displacements have been developed.
Conclusions. New integro-differential relations are proposed based on linear rheological models for the Maxwell medium and the Kelvin medium, including both dynamic and quasi-static models for viscoelastic and elastic media, generalizing the results of previous studies. The proposed constitutive relations of the new form are applicable to describe the thermal response of quasi-elastic bodies of a canonical shape simultaneously in three coordinate systems with a system-defining parameter, which makes it possible to identify the influence of the topology of the region on the value of the corresponding temperature stresses.
- Analytical expressions are obtained and analyzed for determining the phase portrait of the equilibrium structure of a chain of interacting atoms for various values of the parameter characterizing the local potential of the field in which each atom of the chain moves.
- Phase portraits of the equilibrium structure of the system are constructed in continuous and discrete representations of the equilibrium equations for various values of the parameter characterizing the local potential of the field in which each atom of the chain moves.
- It is shown that both periodic and random chaotic arrangements of atoms are implemented depending on the magnitude of the external field.
Objectives. Recently studied phenomena in condensed matter physics have prompted new insights into the dynamic theory of crystals. The results of numerous experimental data demonstrate the impossibility of their explanation within the framework of linear models of the dynamics of many-particle systems, resulting in the necessity to account for nonlinear effects. Analyzing the dynamics of systems in condensed matter physics containing a sufficiently large number of particles shows that modes of motion can undergo changes depending on the potential of interparticle interaction. This is also reflected in the presence of domains with essentially chaotic phase space having a number of degrees of freedom N ≥ 1.5 and a certain set of interparticle interaction parameters. However, it is not only the dynamic model that appears to be strongly nonlinear. A similar nature of motion can be also observed in a static nonlinear many-particle system. The paper aims to study the influence of the external field specified by the interatomic triple-well potential on the equilibrium structure of a chain of interacting atoms.
Methods. Methods of Hamiltonian mechanics are used.
Results. Analytical expressions are obtained and analyzed for determining the phase portrait of the equilibrium structure of a chain of interacting atoms for various values of the parameter characterizing the local potential of the field in which each atom of the chain moves. Phase portraits of the equilibrium structure of the system are constructed in continuous and discrete representations of the equilibrium equations for various values of the parameter characterizing the local potential of the field in which each atom of the chain moves.
Conclusions. It is shown that both periodic and random chaotic arrangements of atoms are implemented depending on the magnitude of the external field.
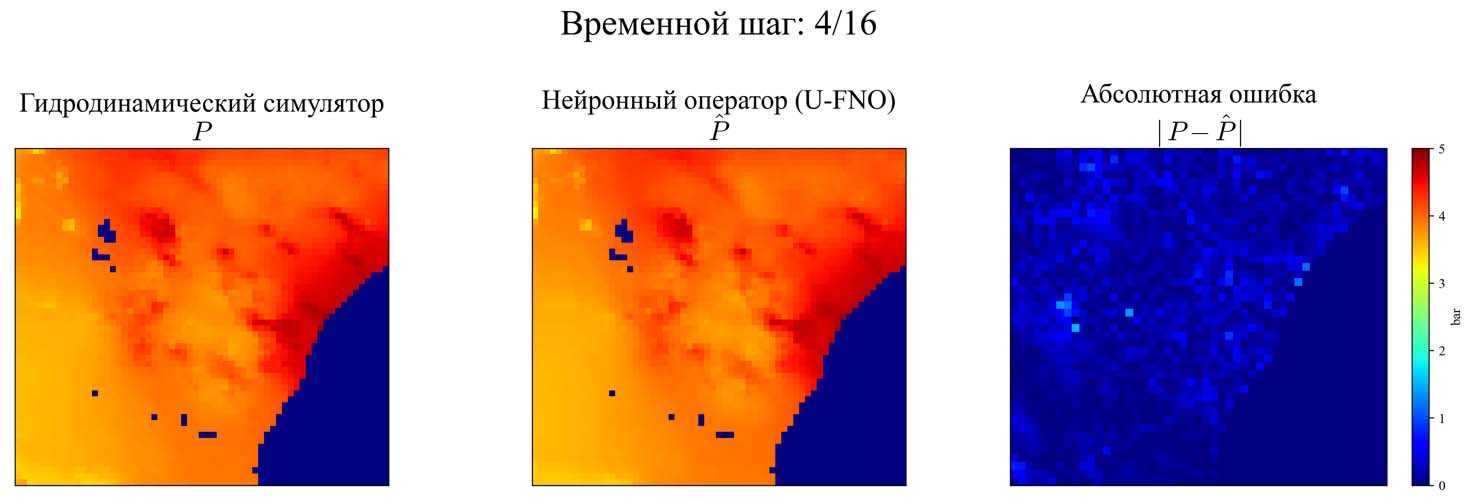
- The aim of the work is to develop a neural operator to speed up calculations involved in hydrodynamic modeling of underground gas storages to an acceptable degree of accuracy.
- A modified Fourier neural operator was built and trained for hydrodynamic modeling of gas filtration processes in underground gas storages.
- The described method is shown to be capable of successful application to problems of three-dimensional gas filtration in a Cartesian coordinate system at objects with many wells.
- The developed model is also effective for modeling objects having a nonuniform grid and complex geometry.
- A trained neural operator can simulate a given scenario in a fraction of a second, which is at least 106 times faster than a traditional numerical simulator.
Objectives. Much of the research in deep learning has focused on studying mappings between finite-dimensional spaces. While hydrodynamic processes of gas filtration in underground storage facilities can be described by partial differential equations (PDE), the requirement to study the mappings between functional spaces of infinite dimension distinguishes this problem from those solved using traditional mapping approaches. One of the most promising approaches involves the construction of neural operators, i.e., a generalization of neural networks to approximate mappings between functional spaces. The purpose of the work is to develop a neural operator to speed up calculations involved in hydrodynamic modeling of underground gas storages (UGS) to an acceptable degree of accuracy.
Methods. In this work, a modified Fourier neural operator was built and trained for hydrodynamic modeling of gas filtration processes in underground gas storages.
Results. The described method is shown to be capable of successful application to problems of three-dimensional gas filtration in a Cartesian coordinate system at objects with many wells. Despite the use of the fast Fourier transform algorithm in the architecture, the developed model is also effective for modeling objects having a nonuniform grid and complex geometry. As demonstrated not only on the test set, but also on artificially generated scenarios with significant changes made to the structure of the modeled object, the neural operator does not require a large training dataset size to achieve high accuracy of approximation of PDE solutions. A trained neural operator can simulate a given scenario in a fraction of a second, which is at least 106 times faster than a traditional numerical simulator.
Conclusions. The constructed and trained neural operator demonstrated efficient hydrodynamic modeling of underground gas storages. The resulting algorithm reproduces adequate solutions even in the case of significant changes in the modeled object that had not occurred during the training process. The model can be recommended for use in planning and decision-making purposes regarding various aspects of UGS operation, such as optimal control of gas wells, pressure control, and management of gas reserves.
ECONOMICS OF KNOWLEDGE-INTENSIVE AND HIGH-TECH ENTERPRISES AND INDUSTRIES. MANAGEMENT IN ORGANIZATIONAL SYSTEMS
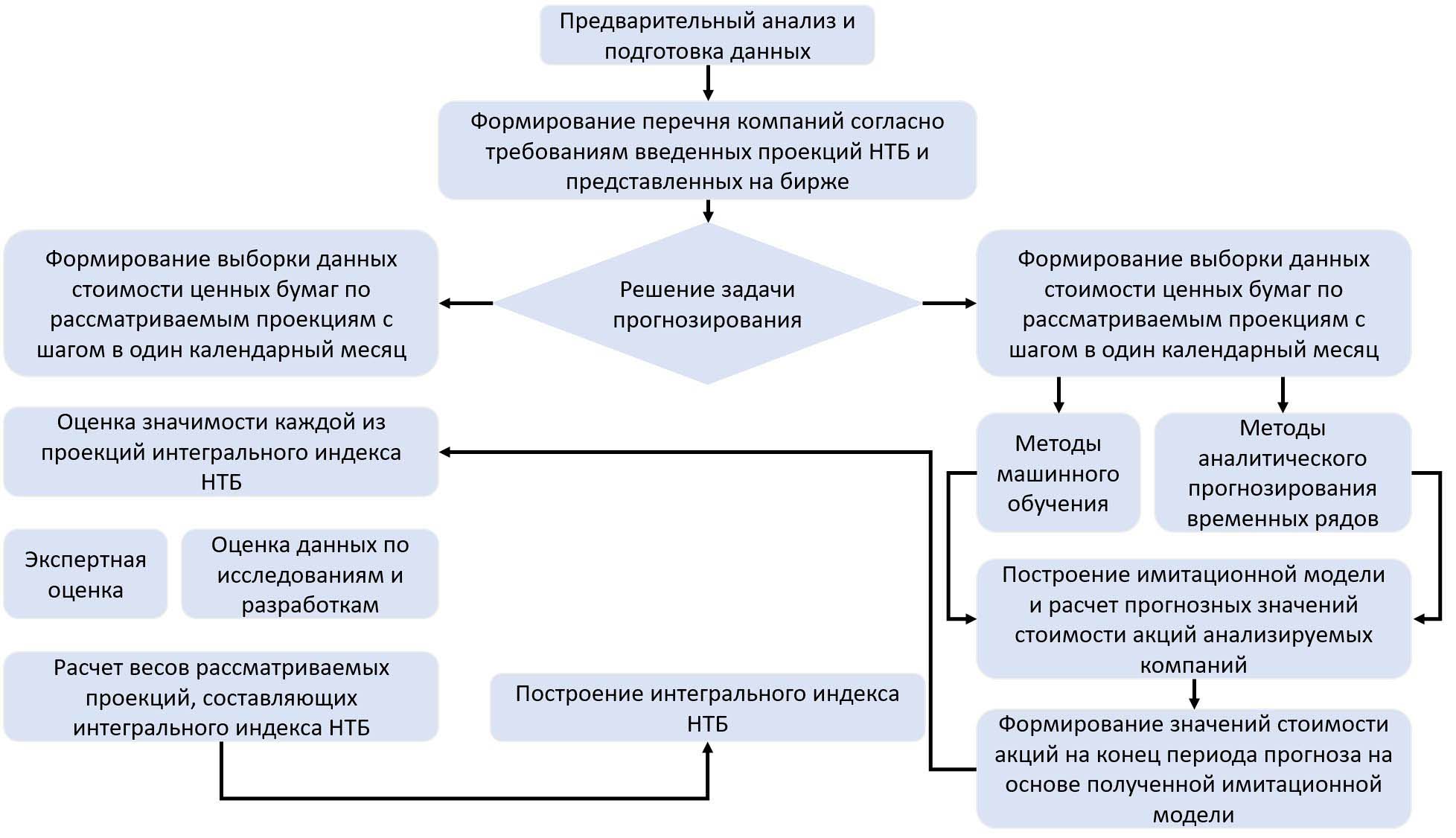
- The approach towards information processing and enhancement of analysis mechanisms in managerial decisions, which relies on diagnostic, analysis, and forecasting tools for socioeconomic system scientific and technological security, is based on information-processing, economic, and mathematical methods.
- The presented results constitute a developed method for the analysis of systemically important enterprises stock indices, supporting research and development to assess and predict scientific and technological security dynamics at meso- and macro levels of the economy.
Objectives. Ensuring scientific and technological sovereignty, defined as one of the objectives of the Concept of Technological Development for the period until 2030, approved by the Order of the Government of the Russian Federation No. 1315-r dated May 20, 2023, implies the use of effective mechanisms for managing the country’s economy. Under contemporary conditions, technology is a crucial element in the country’s economic development and a key component of scientific and technological security. Thus, the aim of the present work is to develop existing methods for analyzing economically significant information relating to the monitoring and diagnostics of scientific and technological security at the meso- and macrolevels.
Methods. The developed method for scientific and technological security level monitoring and forecasting, which is based on the dynamics analysis of the values of corporate securities, includes economic and statistical analysis methods, machine learning and time series analysis tools.
Results. The approach towards information processing and enhancement of analysis mechanisms in managerial decisions, which relies on diagnostic, analysis, and forecasting tools for socioeconomic system scientific and technological security, is based on information-processing, economic, and mathematical methods. The presented results constitute a developed method for the analysis of systemically important enterprises stock indices, supporting research and development to assess and predict scientific and technological security dynamics at meso- and macro levels of the economy. In order to verify the methodology, a numerical experiment was carried out using statistical data from systemically important companies.
Conclusions. The developed methodology is aimed at improved managerial decision-making accuracy and speed when solving problems connected with scientific and technological security underpinning socioeconomic systems. The experimental results quantitatively confirm the significant contribution made by systemically important companies to Russian Federation’s scientific and technological security ensuring.
ISSN 2500-316X (Online)